Dimension 4: Legal and Regulatory Frameworks
This Dimension examines the government’s capacity to design and enact national legislation that directly and indirectly relates to cybersecurity, with a particular emphasis placed on the topics of regulatory requirements for cybersecurity, cybercrime-related legislation and related legislation. The capacity to enforce such laws is examined through law enforcement, prosecution, regulatory bodies and court capacities. Moreover, this Dimension observes issues such as formal and informal co-operation frameworks to combat cybercrime.
Dimension 4. Diagram
Details Research and Directions
Organisations, individuals, and governments need to be confident that their data, computer systems and processes are effectively protected in order to reap the full benefits of cyberspace.
To achieve this, government intervention is sometimes required, for example to oblige private critical infrastructure providers to develop security risk-management plans. We investigate how governments can encourage the development of a secure Internet and online environment using law and regulation.
This Dimension creates a set of resources highlighting best practice in all areas of cybersecurity legislation. Governments across the world are therefore able to use this to improve their legislative framework, identifying areas where they can do more to protect cyberspace and seeing what steps are required to do so.
To create these resources, we examine at a national, regional and international level all the areas of online security that require government action, such as critical national infrastructure, criminal activity, data protection, computer emergency response teams, and education. Criminal activity is one area that receives much attention, but we make sure that we also cover legislation that provides incentives for better protection of data and systems: building more resilient systems, deterring an attack, responding after an incident, and from non-malicious actions, such as losing a laptop.
A key issue is how governments ensure that private critical infrastructure providers meet essential security standards. This is vital because so much of the economy relies on this infrastructure, and breaches can have far-reaching effects. Some countries have asked critical infrastructure providers to voluntarily participate in security standards but there has been limited uptake to date. For the most essential security measures, some governments are considering stronger interventions, and our research examines the best ways to go about this. In the area of cybercrime, as well as considering well documented threats, we look at the use of digital equipment in traditional crimes, for example in theft, and consider how the police can make use of new digital technologies without compromising privacy.
As the effectiveness of laws partially depends on how they are enforced, we also look at the impact of regulatory bodies covering communication and the utilities, and the effectiveness of reporting practices and penalties for data leaks in various countries and regions.
Our research covers laws and regulations at the global, regional and national level. We also examine whether national, regional or international approaches are most appropriate for a particular aspect. To date, we aim to create documents highlighting best practices that will enable policymakers across the world to access knowledge to make decisions on developing effective laws and regulations in their own jurisdictions.
This Dimension is chaired by Professor Federico Varese, Professor of Criminology at the University of Oxford and Senior Research Fellow at Nuffield College, Oxford.
Factors
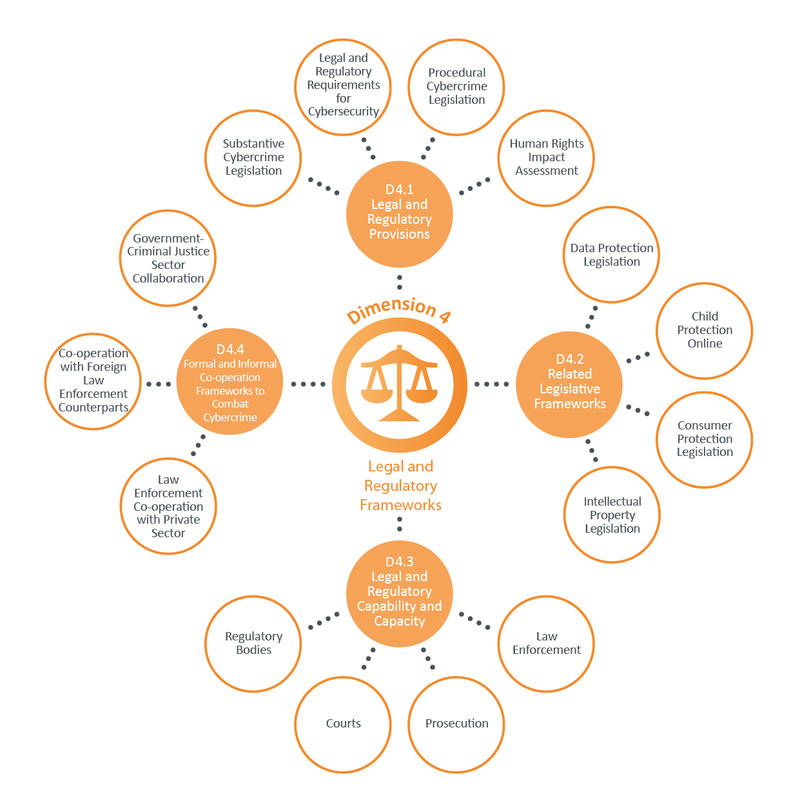
This Factor addresses various legislation and regulatory provisions relating to cybersecurity, including legal and regulatory requirements, substantive and procedural cybercrime legislation, and human rights impact assessment. >
Aspects
- Substantive Cybercrime Legislation: this Aspect explores whether existing legislation criminalises a variety of cybercrimes in specific legislation or general criminal law;
- Legal and Regulatory Requirements for Cybersecurity: this Aspect reviews the existence of legal and regulatory frameworks on cybersecurity;
- Procedural Cybercrime Legislation: this Aspect examines whether comprehensive criminal procedural law–with procedural powers for the investigation of cybercrime and evidentiary requirements to deter, respond to and prosecute cybercrime and crimes involving electronic evidence–is implemented; and
- Human Rights Impact Assessment: this Aspect examines whether human rights impact assessments of substantive and procedural cybercrime legislation and cybersecurity regulations are carried out.
This Factor addresses the legislative frameworks related to cybersecurity including data protection, child protection, consumer protection, and intellectual property.
Aspects
- Data Protection Legislation: this Aspect examines the existence and implementation of comprehensive data protection legislation;
- Child Protection Online: this Aspect focuses on the legislative protection of children online, including the protection of their rights online and the criminalisation of child abuse online;
- Consumer Protection Legislation: this Aspect addresses the existence and implementation of legislation protecting consumers online from fraud and other forms of business malpractice; and
- Intellectual Property Legislation: this Aspect is concerned with the existence and implementation of online intellectual property legislation.
This Factor studies the capacity of law enforcement to investigate cybercrime, the prosecution’s capacity to present cybercrime and electronic evidence cases, and the court’s capacity to preside over cybercrime cases and those involving electronic evidence. Finally, this Factor reviews the existence of cross-sector regulatory bodies to oversee compliance with specific cybersecurity regulations.
Aspects
- Law Enforcement: this Aspect examines whether law enforcement officers and agencies have received training in investigating and managing cybercrime cases, and cases involving electronic evidence, and whether there are sufficient human, procedural and technological resources;
- Prosecution: this Aspect examines whether prosecutors have received training on handling cybercrime cases and cases involving electronic evidence, and whether there are sufficient human, procedural and technological resources;
- Courts: this Aspect examines whether courts have sufficient resources and training to ensure effective and efficient prosecution of cybercrime cases and cases involving electronic evidence; and
- Regulatory Bodies: this Aspect reviews the existence of cross-sector regulatory bodies to oversee compliance with specific cybersecurity regulations.
This Factor addresses the existence and function of formal and informal mechanisms that enable co-operation between domestic actors and across borders to deter and combat cybercrime.
Aspects
- Law Enforcement Co-operation with Private Sector: this Aspect examines the information exchange mechanism on cybercrime between domestic public and private sectors, including co-operation with Internet service and other technology providers;
- Co-operation with Foreign Law Enforcement Counterparts: this Aspect examines the existence of formal mechanisms of international law enforcement co-operation; and
- Government-Criminal Justice Sector Collaboration: this Aspect reviews the formal communication channels between government and criminal justice actors.



